What is a Hacker?
When you hear the phrase “hacker,” you probably picture someone who has malicious intentions toward people, websites, and business information systems. The predominant view is that they try to discard or alter client information while mining corporation data. These “bad people” are genuine; the cybersecurity community refers to them as “Black Hats,” but there are other hackers out there as well.

White Hat Hacker
A white hat hacker usually starts out by trying to find and fix the problem themselves. If that doesn’t work, they may contact the company or person whose computer is being attacked and ask them to fix the problem.
A white hat hacker is someone who uses their hacking skills for good, rather than for evil. They use their skills to protect the public from cyber-attacks and to help people solve their problems.

White hat hackers are usually very careful not to damage or steal information. They usually only hack computers if they think it will help fix the problem or protect people from a cyber-attack.
The Good Guys
Enter the White Hat hacker, the nice individual who, hypothetically, utilises his (or her) skills to hurt your company. The primary goal is to find security flaws in your system so you can better protect your company from risky hackers.
White Hats are employed by businesses to stress test their information systems. They seek to penetrate information systems using techniques Black Hats would employ, perform extensive scans of networks for malware, and even attempt to trick personnel into clicking on links that lead to malware infections.
One of the reasons major firms often have less downtime and website troubles is due to white hats. The majority of hackers are aware that accessing systems run by big firms will be more difficult than systems run by small enterprises, which are likely to lack the capacity to thoroughly check for security flaws.
Because of this, it’s crucial for every online business to ensure that it implements strong preventative measures by deploying reliable firewall software protection, spyware removal solutions, and anti-malware security. Customers must have confidence that internet service providers are safeguarding their data if they don’t, they’ll go elsewhere.
The Ugly
The Gray Hats are the ugly, and they reside between between white and black. Gray Hat hackers often think they’re helping businesses by breaking into their networks and websites without authorization, but business owners rarely welcome intrusions into their information infrastructure.
Most of the time, a Gray Hat’s true motivation is to flaunt his abilities and earn recognition for what he sees as a contribution to cybersecurity.
Frequently, Gray Hats claim that their invasions are harmless. Sometimes, they don’t care about privacy or any other rules; they’re just fascinated about breaking into a well-known system.
According to Gray Hats, making the internet safer for people and businesses is their goal since they believe it isn’t safe for business. To prove their point and spread havoc, they accomplish this through hacking networks and websites.
Most of the time, Gray Hats offer businesses useful information. However, the White Hat community and a large portion of the online community do not consider their techniques to be moral.
The more changes there are
In the United States, neighbours used to frequently leave their doors open. Nowadays, doors are almost never left unattended, and most houses are protected by security alarms. Owners now assume that someone is waiting in the shadows for them to act irresponsibly.
The same realization is dawning on businesses with websites and information systems as it is on households. They are aware that someone is probably watching their online neighborhood and waiting for an opportunity to break in and grab user data.
Black Hat hackers could also wish to install malware that monitors employee and consumer behavior.
Despite the fact that White Hat hackers work as hired guns, continually scanning an organization’s information architecture for dangers, it is still crucial for businesses to take all appropriate precautionary steps. Installing and updating anti-virus software, spyware removal tools, and robust firewall protections are the first steps.
Not simply corporate operations are under jeopardy. The confidentiality of a client’s information and their faith in a company’s honesty are at stake.
Tools and techniques for white-hat hacking
There are many tools and techniques for white-hat hacking. These tools can help you find security vulnerabilities and fix them.
One tool you may use is a vulnerability scanner. A vulnerability scanner checks your computer for security vulnerabilities. You can find vulnerability scanners online or in the software store.
Another tool you may use is a hacker toolkit. A hacker toolkit is a collection of tools that hackers use to break into computers. You can find hacker toolkits online or in the software store.
Another tool you may use is a vulnerability management tool. A vulnerability management tool helps you manage your security vulnerabilities. You can find vulnerability management tools online or you may download them.
Some main Techniques and Tools are:
Pen Testing
Ethical hackers employ their knowledge to find possible points of access and weak areas in the system before attempting to get into the company’s network or publicly accessible system.
Email Phissing
In order to identify and address any problems inside a company’s network before an attack takes place, white hat hackers run genuine anti-phishing campaigns. Email phishing deceives the receiver into opening a malicious attachment or clicking on a link or file that contains sensitive information.

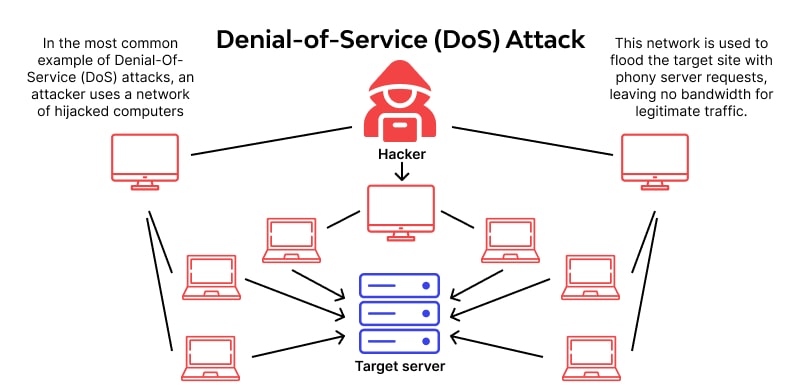
(DOS) Daniel of Service attack
This kind of attack renders a system or network resource momentarily unusable by interfering with or reducing its performance. An organization can create its DoS response strategy with the aid of a white hat hacker who can replicate this kind of assault.
Social Enginering
White hat Hackers evaluate the degree of security of a firm’s systems using behavioral tactics so that the organization can stop an attack. Social engineering attacks use deception to persuade staff members to violate security procedures or divulge private data.
Security Scanning
A range of technologies are used by ethical hackers to automate the process of identifying known vulnerabilities. These include open source pen testing tools like Metasploit Framework or Nikto as well as web application vulnerability detection tools like Acunetix or Netsparker.
How can I become a White Hat hacker
Some white hat hackers were once black hat hackers who developed a stronger sense of ethics as they got older; other white hat hackers who were caught switched to become ethical hackers so they could pursue their goals without fear of being prosecuted.
Although having a sincere interest in and love for security is the best asset, white hat hackers can benefit from having undergraduate or graduate degrees in computer science, information security, or mathematics.
The following accreditations may also be useful for those aspiring white hat hackers:
Certified Ethical Hacker
From EC-Council, a certification that is vendor-neutral and accepted by the US Department of Defense.
- Security Essentials Certification, Advanced Penetration Tester, and Exploit Researcher certifications from the Global Information Assurance Certification
Famous White Hat Hacker
There are several prominent white hat hackers in the field, including:
- Marc Maiffret
- Kevin Mitnick
- Robert “RSnake” Hansen
What legal consequences might white hat hacking cause?
Permission and intent are the main distinctions between a white hat hacker and a black hat hacker. White hat hackers responsibly reveal vulnerabilities and never breach systems without the company’s express written consent. They do this to test the company’s defenses. The tools and methods employed by black hat and white hat hackers are comparable. This may put ethical hackers in challenging legal positions.
For instance, an ethical hacker must attempt to access a firm’s systems both directly and through its business partners in order to comprehensively assess the security of that corporation. The white hat hacker can wind up unlawfully breaking into the systems of the business partner if the firm that sought pen testing does not also seek permission from its business partners.
Additionally, ethical hackers have a responsibility to notify the organization in charge of such data if they are able to obtain important information. The consumer may not, however, always be informed that their information was compromised. It also implies that the data has been seen by the ethical hacker firsthand.


